Your WordPress Site: Addressing Common Security Issues
This page contains affiliate links, which means we may earn a small commission at no cost to you.
Website security is a crucial step that website owners often overlook, sometimes mistakenly believing that a WordPress site is inherently safe. While WordPress itself boasts a secure foundation, it has certain inherent characteristics that, if left unaddressed, can create vulnerabilities. These “openings” can unfortunately be exploited by malicious actors to gain unauthorized access to sensitive information on your website without your knowledge. Interestingly, some of these very features WordPress provides for legitimate purposes, such as API connections and website interoperability, can also be leveraged for unintended uses.
Let’s revise on some common “leaks” you might encounter on a website built with WordPress:
- 1User Enumeration via REST API: Typing yourwebsite.com/wp-json/wp/v2/users in your browser can reveal a list of all registered users on your WordPress site, including the administrator’s username. This information can be a valuable starting point for malicious attempts.
- 2Exposed Login Page: Anyone aware of your website’s address can easily access the administrator login page by simply adding the /wp-admin suffix (e.g., yourwebsite.com/wp-admin). This readily discoverable entry point makes your site a potential target for brute-force attacks, where attackers systematically try numerous password combinations.
- 3Vulnerable XML-RPC: XML-RPC is another component that WordPress often leaves accessible. Visiting yourdomain.com/xmlrpc.php will likely show that it’s open and accepting communication. While designed for legitimate remote management, hackers can exploit this pathway using brute-force techniques to attempt gaining unauthorized access to your site.
- 4Pingback Abuse: While not a direct vulnerability allowing immediate site takeover, pingbacks can have negative consequences. As your site’s traffic grows, you’ll notice notifications called pingbacks appearing, typically in your comment section. These are generated when other websites link to your content. However, this feature can be abused to send a flood of requests to your server, potentially leading to resource exhaustion or being used as part of a larger Distributed Denial of Service (DDoS) attack.
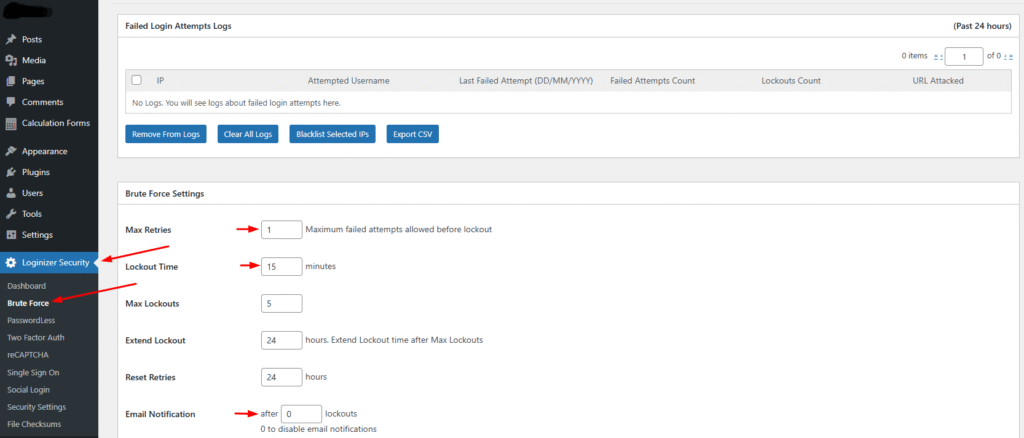
- 5Persistent Brute-Force Threats: Even with a seemingly secure setup, the easily discoverable /wp-admin page remains a constant target for brute-force attacks. Malicious individuals or automated bots can continuously attempt to guess your login credentials.
Fortunately, you can take proactive steps to mitigate these potential issues in your WordPress installation. Here are some quick and effective solutions:
In conclusion, while WordPress provides a solid foundation, proactive security measures are essential to safeguard your website. By understanding these common “openings” and implementing the suggested solutions, you can significantly enhance your WordPress site’s security posture and protect it from potential threats. Remember that website security is an ongoing process, and staying informed about emerging vulnerabilities and best practices is crucial for maintaining a secure online presence.

Get Early Access to Reviews
Get Early Access to Reviews
Subscribe Now for Members-Only Content